For More Info!
Cloud Landing zone
CLOUD LANDING ZONE
Understanding AWS Landing Zones: A Comprehensive Guide
Table of Contents
An AWS landing zone is the foundation for your secure and scalable journey on the Amazon Web Services (AWS) cloud platform.
Imagine it as a well-organized and secure starting point where you can deploy your applications and workloads with confidence. Let’s break it down step-by-step:
1 - Benefits of using AWS Landing Zone
AUTOMATION
Create a secure cloud environment deployable across all AWS Regions, ensuring consistent operations and governance across all AWS areas, including GovCloud (US) and specialized partitions.
DATA SECURITY
Deploy in an AWS Region aligned with your data classification needs and use Amazon Macie for S3 data detection. Utilize AWS KMS for centralized encryption management.
FOUNDATION FOR COMPLIANCE
Utilize a foundational infrastructure to deploy mission-critical workloads within a centrally governed multi-account environment.
2 - How Does an AWS Landing Zone Work?
A landing zone serves as the entry point for your AWS deployments. It’s a meticulously architected multi-account environment designed to handle workloads and applications seamlessly.
This foundation supports essential cloud infrastructure, including:
- Multi-Account Architecture
- Organizational Units (OUs) in AWS Organizations
- Identity and Access Management (IAM)
- Data Security Best Practices

2.1
Multi-Account Architecture
- The core principle is using multiple AWS accounts instead of a single one. Each account can be dedicated to a specific purpose, such as development, testing, or production. This isolation improves security and simplifies access management.
Multi-Account Architecture: The Bedrock
Why Multiple Accounts?
Imagine a single account for all your cloud activities: development, testing, production, storing sensitive data, running public-facing websites – a recipe for security chaos!
Landing zones promote isolation by using separate accounts for each purpose, minimizing the blast radius of a potential security breach.
While the optimal number of AWS accounts may vary based on your needs, a multi-account strategy is a best practice. Segregating resources and workloads across numerous accounts offers several advantages:
- Enhanced Isolation: Fragmenting resources fosters isolation, minimizing the impact of potential security breaches or malfunctions.
- Reinforced Security (Identity & compliance): Compartmentalizing workloads provides an additional security layer to safeguard critical applications.
- Granular (Billing Account) Control: Multiple accounts allow you to separate billing across departments, teams, or individual users.
Account Types
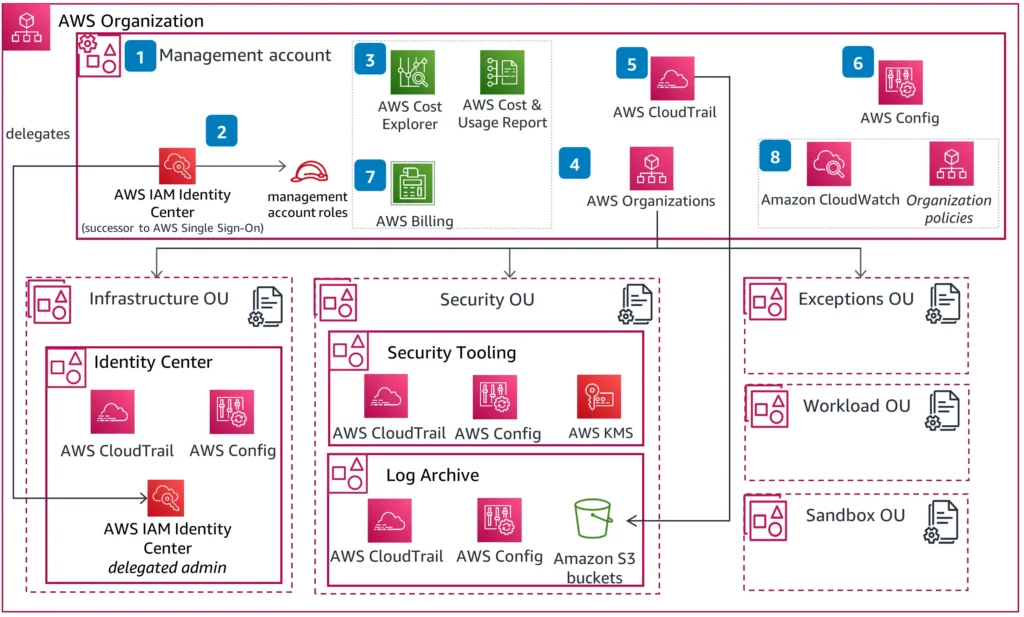
(i) Management Account: The central hub for managing the entire landing zone. It houses services like AWS Organizations and IAM for centralized control.
(ii) Member Accounts: These are the workhorse accounts where you deploy your applications and workloads. You can have multiple member accounts categorized by:
- Function: Development, Testing, Production, Sandbox, etc.
- Department: Finance, Marketing, Engineering, etc.
- Compliance: Accounts dedicated to adhering to specific regulations like HIPAA or PCI DSS.
2.2
Organizational Units (OUs) in AWS Organizations
- This service helps manage your multiple accounts within the landing zone. You can group accounts based on function, department, or any other relevant criteria.
AWS Organizations: Orchestrating the Accounts
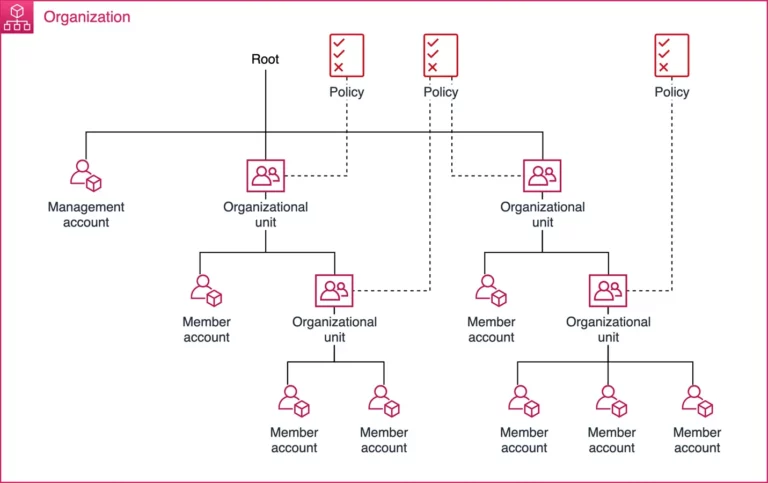
- Create and manage accounts: Easily provision new accounts within your landing zone.
- Group accounts into Organizational Units (OUs): Organize member accounts logically based on function, department, compliance requirements, etc.
- Implement service control policies (SCPs): These are centrally defined policies that apply to all accounts within an OU or the entire organization. They restrict certain actions and enforce security best practices across all accounts.
2.3
Identity and Access Management (IAM)
- IAM allows you to define who has access to which resources in your accounts. You can create IAM users and roles with specific permissions based on the principle of least privilege.
Identity and Access Management (IAM): Granular Control
IAM is the gatekeeper, determining who has access to what resources within your accounts. Here’s how it works:
- Users: Individual people who need access to cloud resources. They can be internal employees or external collaborators.
- Roles: Sets of permissions that define what users can do within an account. Roles are assigned to users based on their job function.
- Groups: A way to manage permissions for multiple users by assigning them to a group with a specific role.
- Policies: Documents that define what actions a user or role can perform on specific resources.
2.4
Data Security Best Practices
- Landing zones are designed to follow AWS best practices for security, such as using strong encryption, logging activity, and continuously monitoring for threats.
Security Best Practices: Building a Fortress
Landing zones are designed to fortify your cloud environment. Some key security practices include:
- Strong Encryption: Data at rest and in transit is encrypted to protect it from unauthorized access.
- Least Privilege: Users and roles are assigned only the minimum permissions they need to perform their jobs.
- Logging and Monitoring: All activities within your accounts are logged and monitored for suspicious behavior.
- Network Segmentation: Virtual Private Clouds (VPCs) and Security Groups isolate resources within your accounts, further reducing risk.
- Regular Updates: Keeping your software and services updated with the latest security patches is crucial.
3 - Deploy the Solution Using AWS
You can efficiently deploy this architecture by utilizing the provided implementation guide along with the accompanying AWS CloudFormation template.
Image Credits: AWS
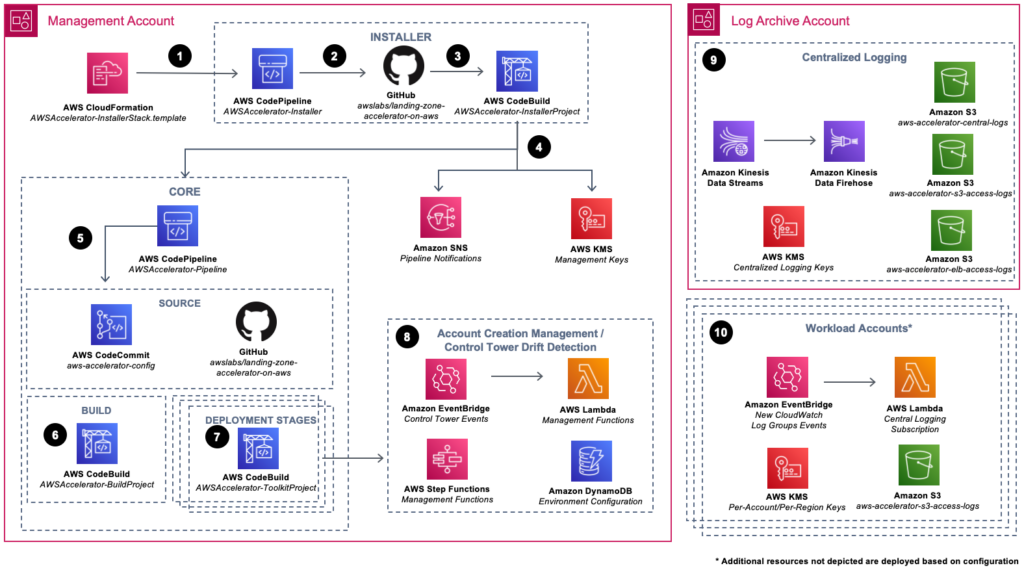
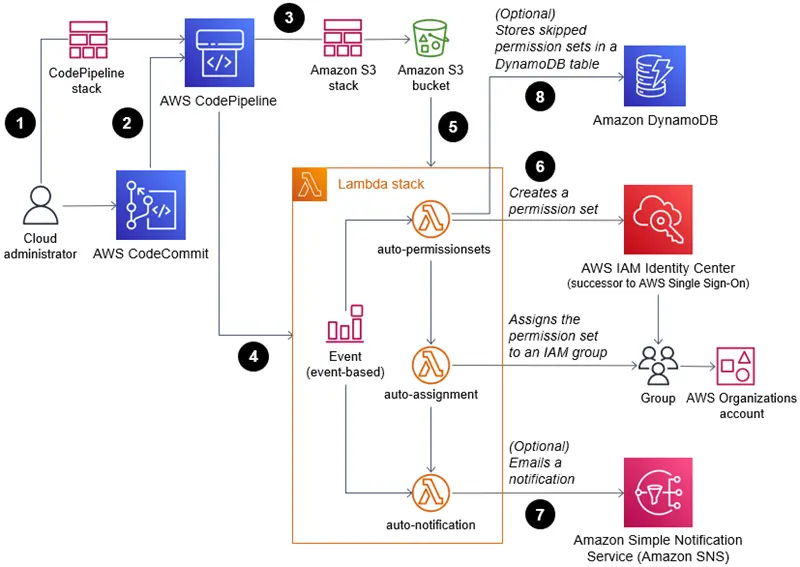
Step 1: Environment Preparation and Deployment
Initialization Begin by leveraging AWS CloudFormation to seamlessly integrate this solution into your environment. Ahead of deployment, ensure that your environment fulfills the necessary prerequisites. The provided CloudFormation template is designed to swiftly deploy an AWS CodePipeline housing the Landing Zone Accelerator on AWS installation engine.
Step 2: Core Feature Deployment
The Installer pipeline orchestrates the deployment of the solution’s core features. This distinct installer operates autonomously from the Core solution infrastructure, facilitating seamless updates to future versions of the solution through a single parameter adjustment via the CloudFormation console.
Step 3: Orchestration and Execution
Utilize an AWS CodeBuild project as the orchestration engine to construct and execute the solution’s AWS Cloud Development Kit (AWS CDK) application. This application is pivotal in deploying CloudFormation stacks across each managed AWS account and respective Regions within the solution framework.
Step 4: Enhanced Observability and Security Measures
Incorporate Amazon Simple Notification Service (Amazon SNS) topics to subscribe to core pipeline events, augmenting observability of Core pipeline operations. Furthermore, integrate two AWS Key Management Service (AWS KMS) customer-managed keys to govern encryption at rest of Installer and Core pipeline dependencies.
Step 5: Input Validation and Stack Deployment
Within the Core pipeline, inputs are meticulously validated and synthesized before deploying supplementary CloudFormation stacks using AWS CDK. Crucially, an AWS CodeCommit repository, named aws-accelerator-config, serves as the repository for the configuration files essential to this solution. These configuration files serve as the cornerstone for configuring and managing the solution, ensuring operational robustness and adaptability.
Step 6: Configuration Validation
Execute a CodeBuild project to compile and validate the solution’s AWS CDK application configuration, ensuring seamless deployment accuracy.
Step 7: Progressive Deployment Stages
Multiple CodeBuild deployment stages are orchestrated to deploy solution configuration-defined resources to your multi-account environment. Optionally include a manual review stage to meticulously assess all impending changes.
Step 8: Drift Detection and Account Automation
Deploy resources dedicated to monitoring AWS Control Tower lifecycle events, swiftly identifying potential drifts from an established optimal state. Additionally, automate the enrollment of new AWS accounts into your multi-account environment for enhanced operational efficiency.
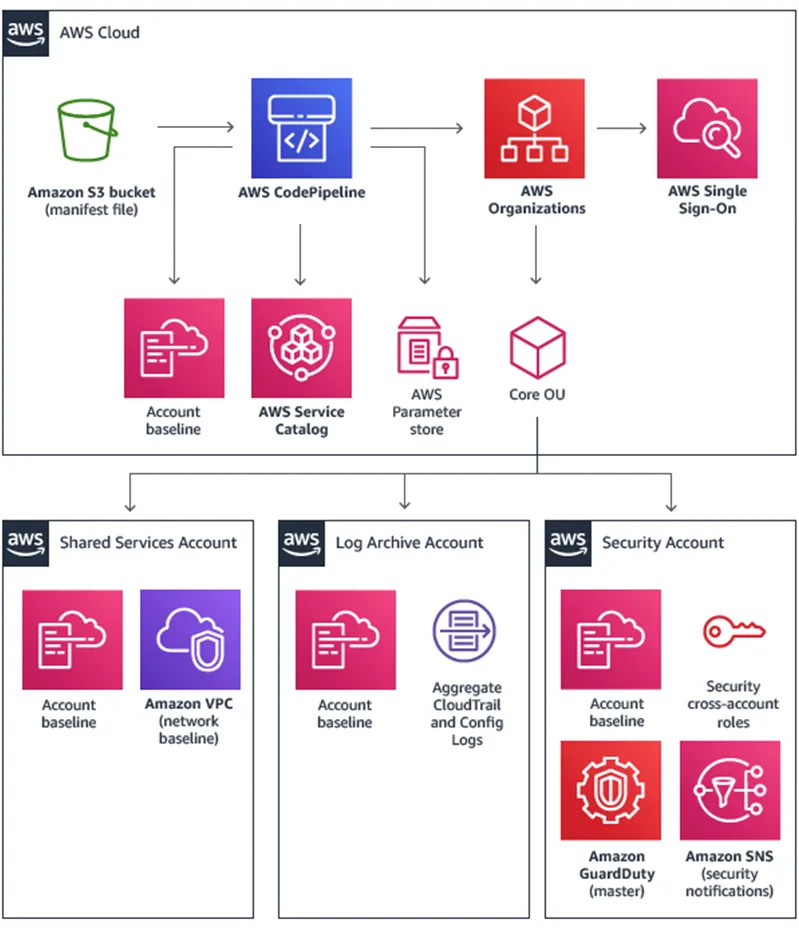
Step 9: Centralized Logging Infrastructure
Establish centralized logging resources within the Log Archive account of your multi-account environment. This includes leveraging Amazon Kinesis resources for streamlined log streaming and ingestion, AWS KMS keys for robust encryption at rest, and Amazon Simple Storage Service (Amazon S3) buckets as designated log storage destinations.
Step 10: Workload Account Enrollment and Provisioning
Efficiently enroll and provision workload accounts into your multi-account environment, augmenting infrastructure as required through the solution’s configuration files. Ensure baseline provisioning includes resources facilitating seamless streaming of Amazon CloudWatch log groups to the centralized logging infrastructure within the Log Archive account.
4
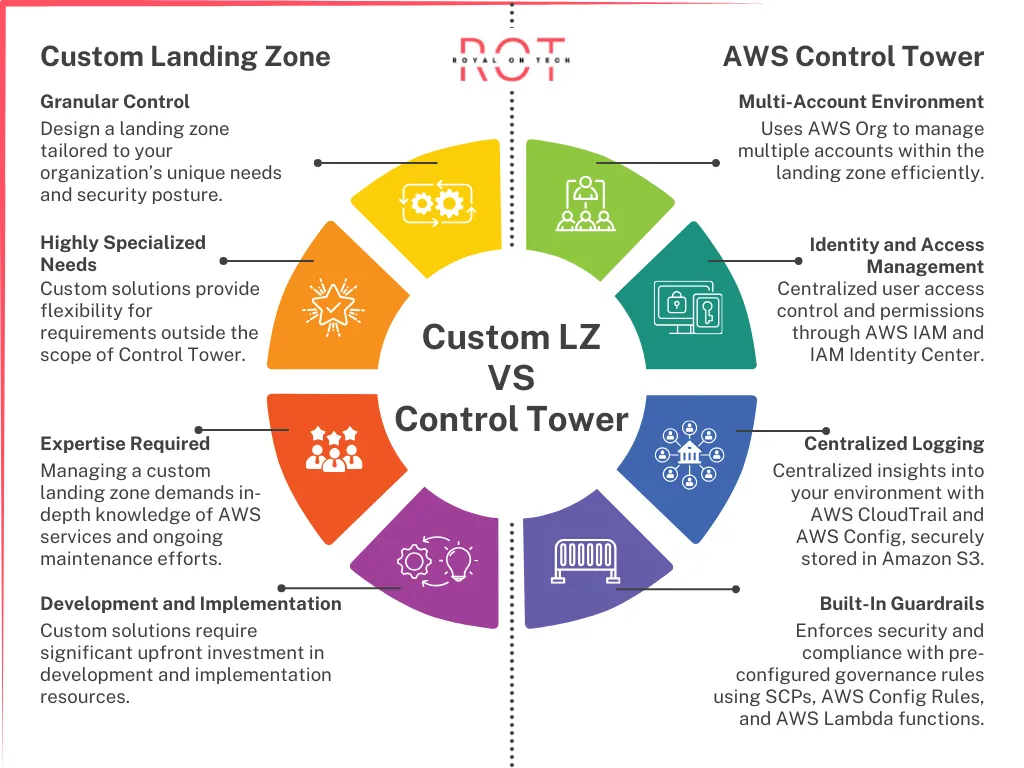
AWS Control Tower vs. Custom Landing Zone
Choosing between Control Tower and a custom landing zone depends on your specific needs.
- AWS Control Tower: Ideal for organizations seeking a fast and secure landing zone with minimal manual configuration. Automated features streamline setup, saving time and minimizing errors.
- Custom Landing Zone: Offers extensive control and customization but requires advanced technical skills for construction and maintenance. This approach is suited for organizations with stringent security or compliance requirements where tailored solutions are necessary.
4 - AWS Control Tower: Automating the Setup (Optional)
Streamlining Landing Zone Creation with AWS Control Tower
Building a secure and compliant AWS landing zone can be a complex task. AWS Control Tower simplifies this process by offering a managed service that automates setup and ongoing management. This guide explores the benefits of Control Tower and its core components.
Why Choose AWS Control Tower?
For organizations seeking a swift and secure approach to landing zone creation, Control Tower is a perfect solution. Here’s what it provides:
- Pre-packaged (Templates) Solution: Eliminate manual configuration with pre-defined, best-practice configurations for your landing zone.
- Automated Setup: Control Tower automates the provisioning of new landing zones, ensuring adherence to industry best practices.
- Centralized Management: Gain a central dashboard to monitor your landing zone’s health, compliance status, and overall well-being.
- Built-In Guardrails: Pre-configured governance rules enforce security and ensure compliance within your environment.
- Effortless Account Creation: The built-in account factory functionality facilitates the creation of new accounts within the landing zone.
- Customizability (Limited): While Control Tower follows a prescriptive approach, some customization is possible through the ‘Customizations for AWS Control Tower’ solution.
Core Components of a Control Tower Landing Zone
A Control Tower landing zone is built on several key components:
- Multi-account Environment: Leverages AWS Organizations to establish a foundation of multiple accounts within your landing zone.
- Identity and Access Management: Centralized control over user access and permissions is achieved through AWS IAM and IAM Identity Center.
- Federated Access: Simplified access management with federated authentication using existing credentials from external identity providers.
- Centralized Logging: Gain comprehensive insights into your environment through centralized logging with services like AWS CloudTrail and AWS Config, securely stored in Amazon S3.
- Enhanced Security with Guardrails: Pre-defined guardrails implement preventive measures (Service Control Policies – SCPs) and detective measures (AWS Config Rules and AWS Lambda functions) to ensure a secure environment.
Custom Landing Zone vs. Control Tower: Choosing Your Path
The best approach for establishing your AWS landing zone depends on your specific needs and technical expertise.
- For organizations seeking a swift, secure, and pre-configured landing zone: AWS Control Tower is the recommended choice.
- For organizations with highly specialized needs and in-house AWS expertise: A custom landing zone may be a viable option, but evaluate Control Tower first.
Ultimately, the decision between Control Tower and a custom landing zone should be based on a thorough assessment of your organization’s goals, resources, and long-term cloud strategy. By choosing the right path, you can create a secure and scalable AWS landing zone that supports your cloud journey.
Future Considerations
AWS Control Tower serves as a springboard for your landing zone journey. Remember to adjust your networking strategy, access management controls, and security measures as your environment expands to meet your specific needs.
5 - Custom-Built Landing Zones: Crafting Your Own Path
For organizations with specialized needs or a desire for complete control, a custom-built landing zone may be the preferred approach.
This requires manually building foundational elements for identity and access management, governance, data security, network design, and logging.
Advantages of a Custom Landing Zone:
- Granular Control: Design a landing zone tailored to your organization’s unique needs and security posture.
- Highly Specialized Needs: Custom solutions provide flexibility for requirements outside the scope of Control Tower.
Considerations Before Building Custom:
- Expertise Required: Managing a custom landing zone demands in-depth knowledge of AWS services and ongoing maintenance efforts.
- Development and Implementation: Custom solutions require significant upfront investment in development and implementation resources.
While a custom landing zone offers flexibility, it’s essential to assess whether Control Tower can meet your needs before opting for a custom approach.
6 - Exploring Alternatives: AWS Landing Zone (AWS CloudFormation)
If Control Tower’s customization options fall short of your requirements, consider AWS Landing Zone. This offering leverages AWS CloudFormation templates to provision a customizable landing zone environment.
7 - Why using AWS Landing Zones!
- Security: A landing zone enforces baseline security policies across all your cloud accounts, reducing the risk of security breaches or accidental misconfigurations.
- Governance: It provides a centralized way to manage access controls, resource usage, and compliance within your cloud environment. This helps maintain order and accountability.
- Scalability: As your needs grow, you can easily add new accounts to your landing zone, allowing you to scale your cloud resources efficiently.
- Cost Optimization: A well-structured landing zone helps avoid resource sprawl, where unused services or resources incur unnecessary costs.
- Streamlined Cloud Adoption: Provides a well-defined starting point for your AWS journey.
8 - Additional Considerations
Cost Management: Landing zones can help optimize costs by preventing resource sprawl. You can use AWS Cost Management tools to track your spending and identify areas for potential cost savings.
Compliance: Landing zones can be configured to meet specific compliance requirements, such as HIPAA or PCI DSS. You can use AWS services like AWS Audit Manager and AWS Config to automate compliance checks.
Disaster Recovery: A well-designed landing zone with backups and redundancy can help you recover from outages or disasters with minimal downtime.
9 - The ROT Perspective on AWS Landing Zones
At ROT Cloud, we offer comprehensive cloud services rooted in a strategic approach to landing zones, ensuring a secure and scalable journey for your applications and workloads on the cloud.
1. Benefits of Using ROT Cloud Landing Zones: Experience a seamless and organized starting point, allowing for efficient deployment and operation of your cloud infrastructure.
2. How ROT Cloud Landing Zones Work: Our approach employs a meticulously designed multi-account environment to streamline your deployments, ensuring optimized resource management and enhanced security.
Multi-Account Architecture: We establish separate accounts for different purposes, such as development, testing, and production, to maintain isolation and simplify access control.
Organizational Units (OUs): We use organizational units to group and manage accounts logically based on function, department, or compliance requirements.
Identity and Access Management (IAM): Our IAM policies allow precise control over who can access which resources, adhering to the principle of least privilege.
Data Security Best Practices: We implement strong encryption, logging, and continuous monitoring to secure your data and cloud environment.
3. Deploying ROT Cloud Solutions: Our implementation guide and templates streamline the deployment of your landing zone architecture, ensuring adherence to industry best practices.
4. ROT Cloud Landing Zone Options: We offer choices between ROT Cloud Tower for a quick and automated setup, and custom landing zones for organizations with specialized needs.
ROT Cloud Tower: Ideal for organizations seeking a fast, secure setup with minimal manual configuration and pre-packaged templates.
Custom Landing Zones: Suited for organizations with stringent security or compliance requirements, offering extensive control and customization.
5. Why Choose ROT Cloud Landing Zones?
Security: Our landing zones enforce baseline security policies across all your cloud accounts.
Governance: We provide centralized management of access controls and resource usage.
Scalability: Our landing zones allow you to scale your cloud resources efficiently as your needs grow.
Cost Optimization: A well-structured landing zone helps you avoid unnecessary costs.
6. Additional ROT Cloud Considerations
Cost Management: Track and optimize your spending using ROT Cloud’s cost management tools.
Compliance: Configure your landing zones to meet specific compliance needs, such as HIPAA or PCI DSS.
Disaster Recovery: Implement backups and redundancy to minimize downtime during outages.
Final Thoughts
ROT Cloud’s well-designed landing zones enable your organization to maximize your cloud potential. With secure and scalable foundations, you can confidently deploy applications and workloads to excel in the cloud.
FAQs
An AWS landing zone is a secure, multi-account foundation you build within the Amazon Web Services (AWS) cloud environment. It serves as a starting point for deploying your workloads and applications. Here’s a breakdown of your questions:
What is it?
- A well-architected, secure, and scalable environment with multiple AWS accounts.
- A foundation for deploying and managing your cloud resources efficiently.
Purpose:
- Provides a secure starting point for your AWS journey.
- Follows best practices for account structure, security, and access management.
- Enables centralized governance and easier scaling of your cloud resources.
OCI Landing Zone (similar concept):
- Landing zones exist in other cloud providers like Oracle Cloud Infrastructure (OCI) as well.
- The core function of providing a secure and organized foundation for cloud deployments remains the same.
Launch Date:
- AWS Landing Zone was introduced by AWS in June 2018.
Benefits:
- Security: Enforces baseline security policies across your accounts.
- Governance: Simplifies managing access and resources within the cloud environment.
- Scalability: Easily add new accounts as your needs grow.
- Cost Optimization: Helps avoid resource sprawl and wasted resources.
AWS Control Tower vs. Landing Zone:
- Landing Zone: The broader concept of a secure multi-account foundation.
- AWS Control Tower: A managed service from AWS that helps automate the setup and management of a landing zone according to best practices. You can build your own landing zone without Control Tower, but it requires more manual configuration.
Terminology:
- Landing zone is a common term used across various cloud providers, not specific to AWS.Google Search didn’t find relevant content. Consider researching further to assess the statement.
Using an AWS Landing Zone:
- There are two main approaches:
- AWS Control Tower: Automates setup and management for a faster start.
- Custom Landing Zone: Offers more control and customization but requires more technical expertise.
Azure vs. AWS Landing Zone:
- Both Azure and AWS offer landing zone functionalities.
- Specific features and implementation details might differ, but the core purpose of providing a secure multi-account foundation remains the same.
FOLLOW US
Technology Partners














